Understanding the Transition from Rev. 4 to Rev. 5
The StateRAMP Board of Directors updated the StateRAMP security controls baseline to align with National Institutes of Standards and Technology Special Publication 800-53, Revision 5 (NIST SP 800-53 Rev. 5). The StateRAMP Program Management Office (PMO) updated the StateRAMP documentation and templates to reflect the changes in NIST SP 800-53, Rev. 5, and developed guidance to assist Cloud Service Providers (CSPs) and Assessors (3PAOs) in transitioning to Rev. 5. Please refer to the FAQ page for additional information.

StateRAMP Standards
StateRAMP has selected the NIST 800-53, Rev. 5 framework as the foundation for all applicable standards. This is in part due to the best practice demonstrated by FedRAMP and given that many security frameworks used by state and local governments are generally tied to the NIST 800-53 framework. This framework is applied in the assessment of service provider’s specific products that serve state and local governments and additional public sector organizations.
The following outlines StateRAMP policies that establish StateRAMP security standards and requirements. These policies are adopted and reviewed annually by the StateRAMP Standards and Technical Committee and Board of Directors.
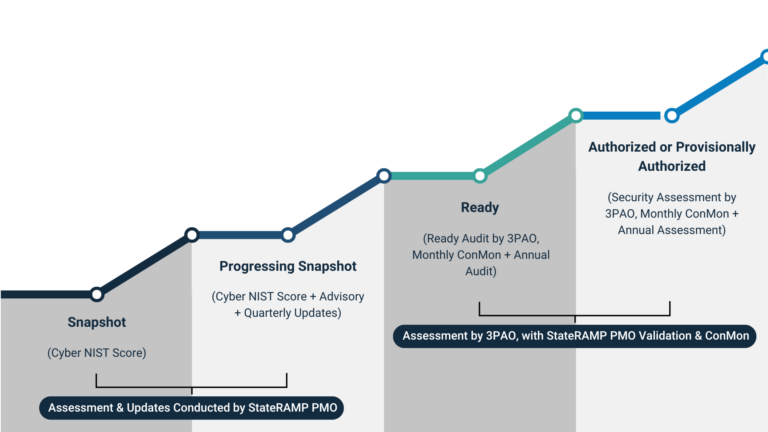
StateRAMP Security Program Risk Acceptance Model
| Rev. 5 Document | Description |
| Security Assessment Framework | Outlines the process and steps required for Cloud Service Providers (CSPs) to undergo a security assessment to meet StateRAMP Rev. 5 standards. This framework guides both CSPs and Third-Party Assessment Organizations (3PAOs) through the assessment and authorization process. |
| Baseline Controls Matrix and Guidance | A comprehensive matrix that provides an overview of the required baseline security controls aligned with NIST 800-53 Rev. 5, including specific guidance on implementing these controls for different impact levels. |
| Security Snapshot Criteria and Scoring | Defines the criteria used to generate a security snapshot of a provider’s system, offering a quick overview of its security posture. This document also explains how scoring is determined based on the implemented controls and potential risks. |
| Procurement Cloud Security Resource Tool | Developed by the NASPO/StateRAMP Procurement Task Force, this tool is designed to help government procurement professionals, risk, and IT experts collaborate effectively, ensuring that cybersecurity is prioritized throughout the procurement process. |
| Ready Minimum Mandatory Requirements for Low Impact Level | Specifies the minimum security requirements that CSPs must meet to achieve StateRAMP “Ready” status for systems categorized as low impact under Rev. 5. This document outlines the initial security baseline for these systems. |
| Ready Minimum Mandatory Requirements for Moderate and High Impact Levels | Details the minimum security requirements for CSPs to reach “Ready” status for systems categorized as moderate and high impact under StateRAMP. These systems face stricter security controls under Rev. 5 to ensure data protection. |
| Baseline Controls by Impact Level for Authorization | Provides a breakdown of the baseline security controls required for StateRAMP authorization, organized by impact level (low, moderate, high). This ensures that CSPs can easily identify the relevant controls for their specific system. |
| Authorization Boundary Guidance | Offers guidance on defining the boundaries of a CSP’s system as it relates to StateRAMP authorization. It helps service providers and assessors determine which parts of a system are in scope for security assessment under Rev. 5. |
| Penetration Test Guidance | Explains the requirements and best practices for conducting penetration testing as part of the StateRAMP security assessment. This document ensures that tests align with Rev. 5 controls and effectively identify vulnerabilities. |
| Continuous Monitoring Guide | Provides instructions on how CSPs should continuously monitor their systems after authorization to maintain compliance with StateRAMP’s Rev. 5 standards. It outlines monitoring activities and reporting requirements to ensure ongoing security. |
| Vulnerability Scan Requirements Guide | A detailed guide on the specific requirements for conducting regular vulnerability scans of CSP systems. This document aligns with Rev. 5 standards to ensure that CSPs proactively identify and address security weaknesses. |
| Incident Communications Procedures | Outlines the procedures that CSPs should follow when communicating with StateRAMP and relevant stakeholders in the event of a security incident. This ensures timely and effective responses in alignment with Rev. 5 standards. |
| Continuous Monitoring Escalation Process Guide | Provides a detailed process for escalating issues identified during continuous monitoring, ensuring that CSPs and assessors address serious risks promptly. It aligns with Rev. 5 to maintain system security and compliance over time. |
We are here to support.
Our team is here to support you through the transition from Rev 4 to Rev 5. If you have any questions or need assistance, please contact us at pmo@stateramp.org.
